| [1] |
M. Agrawal,
N. Kayal, N. Saxena. Primes is in P, http://www.cse.iitk.ac.in/news/primality.pdf.

 |
| [2] |
D. Z. Albert.
On quantum-mechanical automata, Physical
Letters, A 98 (1983), 249–252.

 |
| [3] |
I. Antoniou,
C.S. Calude, M. J. Dinneen (eds.). Unconventional
Models of Computation (UMC’2K), Springer
Verlag, London, 2000.

 |
| [4] |
A. Barenco,
C. H. Bennett, R. Cleve, D. P. DiVincenzo, N. Margoluous, P. W. Schnor, T.
Sleator, J. A. Smolin, H. Weinfurter. Elementary gates of quantum computation,
Physical Review, A 52 (1995), 3457–3467.

 |
| [5] |
A. Barenco.
Quantum Computation, PhD Thesis, Oxford University, 1996.

 |
| [6] |
J. Barrow.
Impossibility–The Limits of Science
and the Science of Limits, Oxford
University Press, Oxford, 1998.

 |
| [7] |
D. Beckman,
A. N. Shari, S. Devabhaktuni, J. Preskill. Efficient networks for quantum
factoring, Physical Review A, 54 (1996), 1034–1063.

 |
| [8] |
J. S. Bell.
On the Einstein Podolsky Rosen paradox, Physics, 1 (1964), 195–200.
Reprinted in [138], 403–408,
and in [9], 14–21.

|
| [9] |
J. S. Bell.
Speakable and Unspeakable in
Quantum Mechanics, Cambridge University
Press, Cambridge, 1987.
 |
| [10] |
P. Benioff.
The computer as a physical system: A microscopic quantum mechanical Hamiltonian
model of computers as represented by Turing machines, Journal of Statistical Physics, 22 (1980), 563–591.

|
| [11] |
C. H. Bennett.
Logical reversibility of computation, IBM
J. Res. Dev., 17 (1973), 525–532.

 |
| [12] |
C. H. Bennett.
The thermodynamics of computation, International
Journal of Theoretical Physics, 21
(1982), 905–940.

 |
| [13] |
C. H. Bennett.
Demons, engines and the second law, Scientific
American, November (1987), 108–116.

 |
| [14] |
C. H. Bennett.
Notes on the history of reversible computation, IBM J. Res. Dev., 32 (1988), 281–288.

 |
| [15] |
C. H. Bennett.
Time/space trade-offs for reversible computation, SIAM J. on Computing, 18 (1989), 766–776.

 |
| [16] |
C. H. Bennett,
E. Bernstein, G. Brassard, U. Vazirani. Strengths and weaknesses of quantum
computing, quant-ph/9701001.
 |
| [17] |
C. H. Bennett,
G. Brassard, C. Crepeau, R. Jozsa, A. Peres, W. K. Wootters. Teleporting
an unknown quantum state via dual classical and Einstein-Podolsky-Rosen channels,
Phys. Rev. Lett., 70 (1993), 1895–1898.

|
| [18] |
C. H. Bennett,
R. Landauer. The fundamental physical limits of computation, Scientific American, July (1985), 48–56.

|
| [19] |
G. P. Berman,
G. D. Doolen, R. Mainieri, V. I. Tsifrinovich. Introduction to Quantum Computers, World Scientific, Singapore, 1993.

 |
| [20] |
G. Birkhoff,
J. von Neumann. The logic of quantum mechanics, Annals of Mathematics, 37(4) (1936), 823–843.

 |
| [21] |
D. Bouwmeester,
J.-W. Pan, H. Weinfurter, A. Zeilinger. High-fidelity teleportation of independent
qubits, quant-ph/9910043.

|
| [22] |
G. Brassard.
Searching a quantum phone book, Science, 31 January (1997), 627–628.

 |
| [23] |
W. Brauer,
Automatentheorie, Teubner, Stuttgart, 1984.

 |
| [24] |
M. Brooks
(ed.). Quantum Computing and Communications, Springer-Verlag, Berlin, 1999.

 |
| [25] |
V. Buzek,
S. L. Braunstein, M. Hillery, D. Bru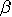 . Quantum copying: a network, Physical Review A, 56,5 (1997), 3446–3452. . Quantum copying: a network, Physical Review A, 56,5 (1997), 3446–3452.

|
| [26] |
C. Calude.
Theories of Computational Complexity, North-Holland, Amsterdam, 1988.

 |
| [27] |
C. Calude.
Information and Randomness. An
Algorithmic Perspective, 2nd Edition,
Revised and Extended, Springer Verlag, Berlin, 2002.

|
| [28] |
C. S. Calude,
E. Calude, K. Svozil, S. Yu. Physical versus computational complementarity
I, International Journal of Theoretical
Physics, 36, 7 (1997), 1495–1523.

|
| [29] |
C. S. Calude,
E. Calude, K. Svozil. Quantum correlations conundrum: An automaton-theoretic
approach, in G. Paun, ed., Recent Topics
in Mathematical and Computational Linguistics, Romanian Academy Publishing Company, Bucharest,
2000, 55–67.

|
| [30] |
C. S. Calude,
J. L. Casti. Parallel thinking, Nature
392, 9 April (1998), 549–551.

 |
| [31] |
C. S. Calude,
J. L. Casti. Silicon, molecules, or photons? Complexity, 4, 1 (1998),
13.

|
| [32] |
C. S. Calude,
J. L. Casti (eds.). Unconventional
Models of Computation, Complexity, Vol. 4, 1, (1998), 13–42. (special issue)

|
| [33] |
C. S. Calude,
J. Casti, M. J. Dinneen (eds.). Unconventional
Models of Computation, Springer-Verlag,
Singapore, 1998.

|
| [34] |
C. S. Calude,
G. J. Chaitin. Randomness everywhere, Nature, 400, 22 July (1999), 319–320.

 |
| [35] |
C.S. Calude,
M. J. Dinneen, F. Peper (eds.). Unconventional
Models of Computation (UMC’02), Lecture
Notes Comput. Sci. 2509, Springer Verlag, Heidelberg, 2002.

|
| [36] |
C. S. Calude,
M. J. Dinneen, K. Svozil. Reflections on quantum computing, Complexity, 6, 1 (2000), 35–37.

 |
| [37] |
C. S. Calude,
P. H. Hertling, K. Svozil. Embedding quantum universes into classical ones,
Foundations of Physics, 29, 3 (1999), 349–379.

|
| [38] |
C. S. Calude,
M. Lipponen. Computational complementarity and sofic shifts, in X. Lin, ed.,
Theory of Computing 98, Proceedings
of the 4th Australasian Theory Symposium, CATS’98, Springer-Verlag, Singapore, 1998, 277–290.

|
| [39] |
C. S. Calude,
G. Paun. Computing with Cells and Atoms, Taylor & Francis Publishers, London, 2001.

|
| [40] |
C. S. Calude,
B. Pavlov. Coins, quantum measurements, and Turing’s barrier, Quantum Information Processing 1, 1–2 (2002), 107–127.

|
| [41] |
E. Calude,
Automata-Theoretic Models for
Computational Complementarity, PhD
Thesis, The Univ. of Auckland, 1998.

|
| [42] |
G. J. Chaitin.
Information, Randomness and Incompleteness,
Papers on Algorithmic Information Theory, World Scientific, Singapore, 1987. (2nd ed., 1990).

|
| [43] |
G. J. Chaitin.
The Limits of Mathematics, Springer-Verlag, Singapore, 1997.

|
| [44] |
J. F. Clauser,
A. Shimony. Bell’s theorem: experimental tests and implications, Rep. Prog. Phys., 41 (1978), 1821–1927.

|
| [45] |
D. W. Cohen.
An Introduction to Hilbert Space
and Quantum Logic, Springer-Verlag,
New York, 1989.

|
| [46] |
J. H. Conway.
Regular Algebra and Finite Machines, Chapman and Hall, London, 1971.

 |
| [47] |
K. De Leeuw,
E. F. Moore, C. E. Shannon, N. Shapiro. Computability by probabilistic machines,
in C. E. Shannon, J. McCarthy (eds.), Automata
Studies, Princeton University Press,
Princeton, N.J., 1956, 183–212.

|
| [48] |
D. Deutsch.
Quantum theory, the Church-Turing principle and the universal quantum computer,
Proceedings of the Royal Society
London, A 400 (1985), 97–119.

|
| [49] |
D. Deutsch.
Quantum computation, Physics World, 5 (1992), 57–61.

|
| [50] |
D. Deutsch.
The Fabric of Reality, Allen Lane, Penguin Press, 1997.

|
| [51] |
D. Deutsch,
A. Barenco, A. Ekert. Universality in quantum computation, Proceedings of the Royal Society of London, A 449 (1995), 669–677.

|
| [52] |
D. Deutsch,
R. Josza. Rapid solution of problems by quantum computation, Proceedings of the Royal Society London, A 439 (1992), 553–558.

 |
| [53] |
D. Dieks.
Communication by EPR devices, Physical
Letters A, 92 (1982), 271–272.

 |
| [54] |
P. Dirac.
The Principles of Quantum Mechanics, 4th ed., Oxford University Press, Oxford, 1958.

|
| [55] |
A. Einstein,
B. Podolsky, N. Rosen. Can quantum-mechanical description of physical reality
be considered complete? Physical Review, 47 (1935), 777–780. Reprinted in [138], 138–141.

|
| [56] |
A. Ekert,
R. Jozsa. Shor’s quantum algorithm for factoring numbers, Rev. Modern Physics 68 (3), (1996), 733–753.

 |
| [57] |
G. Etesi,
I. Németi. Non-Turing computations via Malament-Hogarth space-times,
International Journal of Theoretical
Physics 41 (2002), 341–370. Los Alamos
preprint archive http: //arXiv:gr-qc/0104023, v1, 9 April 2001.

|
| [58] |
R. P. Feynman.
Simulating physics with computers, International
Journal of Theoretical Physics, 21
(1982), 467–488.

|
| [59] |
R. P. Feynman.
Quantum mechanical computers, Optics
News 11 (1985), 11–20.

|
| [60] |
R. P. Feynman,
in D. H. Gilbert (eds.). Miniaturization, Reinhold, New York, 1961, 282–296.

|
| [61] |
Feynman Lectures on Computation, J. G. Hey and R. W. Allen, eds., Addison-Wesley,
Reading, Massachusetts, 1996.

 |
| [62] |
D. Finkelstein,
S. R. Finkelstein. Computational complementarity, International Journal of Theoretical Physics, 22, 8 (1983), 753–779.

|
| [63] |
E. Fredkin,
T. Toffoli. Conservative logic, International
Journal of Theoretical Physics, 21
(1982), 219–253.

|
| [64] |
D. M. Greenberger,
M. A. Horne, A. Zeilinger. Going beyond Bell’s theorem, in M. Kafatos (ed.).
Bell’s Theorem, Quantum Theory,
and Conceptions of the Universe, Kluwer
Academic Publishers, Dordrecht, 1989, 73–76.

|
| [65] |
D. M. Greenberger,
A. YaSin. “Haunted” measurements in quantum theory, Foundation of Physics, 19, 6 (1989), 679–704.

|
| [66] |
L. K. Grover.
A fast quantum mechanical algorithm for database search, Proceedings of the Twenty-Eighth Annual ACM Symposium
on the Theory of Computing, 1996,
212–219.

|
| [67] |
J. Gruska.
Quantum Computing, McGraw-Hill, London, 1999.

|
| [68] |
G. H. Hardy,
E. M. Wright. An Introduction to the
Theory of Numbers, Oxford University
Press, Oxford (4th edition), 1965.

|
| [69] |
H. Havlicek,
K. Svozil. Density conditions for quantum propositions, Journal of Mathematical Physics, 37(11) (1996), 5337–5341.

|
| [70] |
T. J. Herzog,
P. G. Kwiat, H. Weinfurter, A. Zeilinger. Complementarity and the quantum
eraser, Physical Review Letters, 75, 17 (1995), 3034–3037.

|
| [71] |
J. G. Hey
(ed.). Feynman and Computation. Exploring
the Limits of Computers, Perseus Books,
Reading, Massachusetts, 1999.

|
| [72] |
M. Hirvensalo.
An introduction to quantum computing, Bulletin
of the EATCS, 66 (1998), 100–121.

|
| [73] |
M. Hogarth.
Predicting the future in relativistic spacetimes, Studies in History and Philosophy of Science. Studies
in History and Philosophy of Modern Physics 24, 5 (1993), 721–739.

|
| [74] |
T. Hogg. Highly
structured searches with quantum computers, Physical Review Letters, 80 (1998) 2473–2476.

 |
| [75] |
R. J. Hughes.
Cryptography, quantum computation and trapped ions, Technical Report LA-UR-97-4986, Los Alamos National Laboratory, 1997.

|
| [76] |
J. Jarett.
On the physical significance of the locality condition in Bell argument,
Noûs, 18 (1984), 569–589.

|
| [77] |
E. Jurvanen,
M. Lipponen. Distinguishability, simulation and universality of Moore tree
automata, Fundamenta Informaticae, 34 (1999), 1–13.

|
| [78] |
G. Kalmbach.
Orthomodular Lattices, Academic Press, New York, 1983.

 |
| [79] |
T.D. Kieu.
Quantum algorithm for the Hilbert’s tenth problem, Los Alamos preprint archive
http://arXiv:quant-ph/0110136, v2, 9 November 2001.

|
| [80] |
S. Kochen,
E. P. Specker. The problem of hidden variables in quantum mechanics, Journal of Mathematics and Mechanics, 17(1) (1967), 59–87. Reprinted in [126], 235–263.

|
| [81] |
R. Landauer.
Irreversibility and heat generation in the computing process, IBM J. Res. Develop., 5 (1961), 183–191.

|
| [82] |
R. Landauer.
Computation, measurement, communication and energy dissipation, in S. Haykin
(ed.). Selected Topics in Signal Processing, Prentice Hall, Englewood Cliffs, New Jersey, 1989,
18.

|
| [83] |
R. Landauer.
Information is physical, Physics Today,
_44 (1991), 23–29.

|
| [84] |
R. Landauer.
Information is inevitably physical, in [71
], 76–92.

|
| [85] |
R. Landauer.
Information is physical, but slippery, in [24
], 59–62.

|
| [86] |
H. S. Leff,
A. F. Rex. Maxwell’s Demon: Entropy,
Information, Computing, Princeton
University Press, Princeton, 1990.

|
| [87] |
A. Lenstra,
H. Lenstra (eds.). The Development
of the Number Field Sieve, Springer-Verlag,
New York, 1993.

|
| [88] |
S. Lloyd.
Almost any quantum gate is universal. Phys.
Rev. Letters, 75 (1995), 346–349.

 |
| [89] |
S. Lloyd.
Quantum-mechanical Maxwell’s demon, Phys.
Rev., A56 (1997), 3374–3382.

|
| [90] |
H-K. Lo, H.
F. Chau. Is quantum bit commitment really possible? Phys. Rev. Lett., 78 (1997), 3410–3413.

|
| [91] |
H-K. Lo, T.
Spiller, S. Popescu (eds.). Introduction
to Quantum Computation and Information, World Scientific, Singapore, 1999.

|
| [92] |
G. W. Mackey.
Quantum mechanics and Hilbert space, Amer.
Math. Monthly, Supplement, 64 (1957),
45–57.

|
| [93] |
C. Macchiavello,
G. M. Palma, A. Zeilinger (eds.). Quantum
Computation and Quantum Information Theory, Collected Papers and Notes, World Scientific, Singapore, 1999.

|
| [94] |
J. C. Maxwell.
Theory of Heat, Longman’s, Green, & Co., London, 1985, 328–329.

 |
| [95] |
D. Mayers.
Unconditionally secure quantum bit commitment is impossible, Phys. Rev. Lett., 78 (1997), 3414–3417.

 |
| [96] |
Z. Meglicki.
Introduction to Quantum Computing
(M743), Indiana University, April
2, 2002, 264 pp.

|
| [97] |
N. D. Mermin.
Bringing home the atomic world: Quantum mysteries for anybody, American Journal of Physics, 49 (1981), 940–943.

|
| [98] |
N. D. Mermin.
Quantum mysteries revisited, American
Journal of Physics, 58 (1990), 731–734.

|
| [99] |
N. D. Mermin.
Hidden variables and the two theorems of John Bell, Reviews of Modern Physics, 65 (1993), 803–815.

|
| [100] |
A. Messiah.
Quantum Mechanics, Volume 1, North-Holland, Amsterdam, 1961.

|
| [101] |
G. Milburn.
Quantum optical Fredkin gate, Physical
Review, 62 (1989), 2124–2127.

|
| [102] |
G. Milburn.
The Feynamn Processor. An Introduction
to Quantum Computation, Allen &
Unwin, St. Leonards, 1998.

|
| [103] |
G. Mitchison,
R. Josza. Counterfactual computation, quant-ph/9907007.

|
| [104] |
E. F. Moore.
Gedanken-experiments on sequential machines, in C. E. Shannon and J. McCarthy
(eds.). Automata Studies, Princeton University Press, Princeton, 1956, 128–153.

|
| [105] |
M. A. Nielsen,
I. L. Chuang. Quantum Computation and
Quantum Information, Cambridge University
Press, 2002, 2nd printing.

|
| [106] |
P. Odifreddi.
Classical Recursion Theory, North-Holland, Amsterdam, New York, Vol. 1, 1989,
Vol. 2, 1999.

 |
| [107] |
P. Odifreddi.
Indiscrete applications of discrete mathematics, in D. S. Bridges, C. S.
Calude, J. Gibbons, S. Reeves, I. Witten (eds.). Combinatorics, Complexity, Logic, Springer-Verlag, Singapore, 1996, 52–65.

|
| [108] |
M. Ohya, I.
V. Volovich. A new quantum algorithm for NP-complete problems, CDMTCS Research Report 194 (2002), 10 pp.

|
| [109] |
A. Peres.
Einstein, G ödel, Bohr, Foundations
of Physics, 15 (1985), 201–205.

|
| [110] |
A. Peres.
Quantum Theory: Concepts and
Methods, Kluwer Academic Publishers,
Dordrecht, 1993.

|
| [111] |
I. Prigogine.
From Being to Becoming, W. H. Freeman, San Francisco, 1980.

|
| [112] |
P. Pták,
S. Pulmannová. Orthomodular
Structures as Quantum Logics, Kluwer
Academic Publishers, Dordrecht, 1991.

 |
| [113] |
M. O. Rabin.
Probabilistic algorithms, in [135], 21–39.

 |
| [114] |
T. Rado. On
non-computable functions, Bell System
Technical Journal 41 (1962), 877–884.

 |
| [115] |
D. J. Foulis,
C. H. Randall. Operational statistics. I. Basic concepts, Journal of Mathematical Physics, 13 (1972), 1667–1675.

 |
| [116] |
H. Reichenbach.
The Direction of Time, University of California Press, LA, 1956.

|
| [117] |
E. Rieffel,
W. Polak. An introduction to quantum computing for non-physicists, quant-ph/9809016.

|
| [118] |
R. Rivest,
A. Shamir, L. Adleman. A method for obtaining digital signatures and public
key cryptosystems, Communications of
ACM, 21 (1978), 120–126.

|
| [119] |
A. Salomaa.
Public-Key Cryptography, Springer-Verlag, Berlin, 1996.

|
| [120] |
B. Schumaker.
Quantum coding, Physical Review A, 51, 4 (1995), 2738–2747.

|
| [121] |
C. E. Shannon,
Computers and automata, Proceedings
of the I. R. E. 41 (1953), 1235–1241.

|
| [122] |
P. W. Shor.
Algorithms for quantum computation: discrete log and factoring, Proceedings of the 35th IEEE Annual Symposium on
Foundations of Computer Science, 1994,
124–134.

|
| [123] |
H. T. Siegelmann.
Computation beyond the Turing limit, Science, 268 (April 1995), 545–548.

|
| [124] |
H. T. Siegelmann.
Neural Networks and Analog Computation:
Beyond the Turing Limit, Birkhauser,
Boston, MA, 1999.

|
| [125] |
E. Specker.
Die Logik nicht gleichzeitig entscheidbarer Aussagen, Dialectica, 14 (1960), 175–182. Reprinted in [126], 175–182.

|
| [126] |
E. Specker.
Selecta, Birkhäuser Verlag, Basel, 1990.

 |
| [127] |
A. Steane.
Quantum computing, quant-ph/9708022.

|
| [128] |
K. Svozil.
Randomness & Undecidability
in Physics, World Scientific, Singapore,
1993.

|
| [129] |
K. Svozil.
Quantum Logic, Springer-Verlag, Singapore, 1998.

|
| [130] |
K. Svozil.
The Church-Turing Thesis as a guiding principle for physics, in [33], 371–385.

 |
| [131] |
K Svozil.
One-to-one, Complexity, 4 (1) (1998), 25–29.

|
| [132] |
L. Szilard.
On the decrease of entropy in a thermodynamic system by the intervention
of intelligent beings, Zeitschrift
für Physics, 53 (1929), 840–856.

|
| [133] |
M. Tegmark,
J. A. Wheeler. 100 years of quantum mysteries, Scientific American February
(2001), 68–75.

 |
| [134] |
T. Toffoli,
N. Margolus. Cellular Automata Machines, MIT Press, Cambridge, MA, 1987.

 |
| [135] |
J. Traub.
Algorithms and Complexity: New
Directions and Results, Academic Press,
London, 1976.

|
| [136] |
A. M. Turing.
On computable numbers, with an application to the Entscheidungsproblem, Proc. London Math. Soc., Ser. 2, 42 (1936), 230–265; a correction, 43 (1936),
544–546.

|
| [137] |
H. Weyl. Philosophy of Mathematics and Natural Science, Princeton University Press, Princeton, 1949.

|
| [138] |
J. A. Wheeler,
W. H. Zurek. Quantum Theory and Measurement, Princeton University Press, Princeton, 1983.

|
| [139] |
U. Vazirani.
Quantum computing, 1997, (http://www.cs.berkeley.edu/vazirani.)

|
| [140] |
C. P. Williams,
S. H. Clearwater. Explorations in Quantum
Computing, Springer-Verlag, New York,
1997.

 |
| [141] |
C. P. Williams,
S. H. Clearwater. Ultimate Zero and
One: Computing at the Quantum Frontier, Springer-Verlag, Heidelberg, 2000.

|
| [142] |
W. K. Wooters,
W. H. Zurek. A single quantum cannot be cloned, Nature,
299 (1992), 802–803.

|
| [143] |
A. Yao. Quantum
circuit complexity, Proceedings of
the 34th IEEE Symposium on Foundations of Computer Science (FOCS), IEEE Computer Science Press, Los Alamitos, 1993,
352–260.

|
| [144] |
C. Zalka.
Grover’s quantum searching algorithm is optimal, quant-ph/9711070.

|
| [145] |
W. H. Zurek.
Algorithmic randomness, physical entropy, measurements, and the Demon of
choice, in [71], 393–410.
 |










































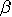 . Quantum copying: a network, Physical Review A, 56,5 (1997), 3446–3452.
. Quantum copying: a network, Physical Review A, 56,5 (1997), 3446–3452. 

















































































































































